Flood Shield는 분산 서비스 거부 공격(예: SYN Flood, ACK Flood, UDP Flood, HTTP Flood 등)으로부터 오리진의 안정성을 보장하기 위해 빠르고 간단하며 효과적인 DDoS 보호를 제공하는 포괄적인 클라우드 기반 DDoS 보호 서비스입니다. .) 실시간. 동시에 합법적인 사용자에게 가속화 서비스를 제공하여 전반적인 고객 경험을 최적화합니다. 이 솔루션은 온라인 서비스 및 인프라의 안정성과 신뢰성을 보장하는 방패 역할을 합니다.
Flood Shield는 미국, 유럽, 아시아 및 중국 본토에 데이터 센터가 있는 CDNetworks의 거대한 글로벌 인프라에 배포됩니다. 20개가 넘는 글로벌 DDoS 스크러빙 센터와 15Tbps의 총 용량을 갖춘 이 제품은 가장 정교하고 대규모의 볼류메트릭 공격으로부터 웹 사이트, 웹 앱 및 네트워크 인프라를 보호하도록 설계되었습니다.
20개 이상의 글로벌 DDoS 스크러빙 센터
15Tbps 이상의 완화 용량
SYN Flood, ACK Flood, ICMP Flood, UDP Flood, HTTP Flood, SlowLoris attack 등을 포함한 Layer 3/4 및 Layer 7 DDoS 방어
액세스 정책 및 속도 제한을 사전에 정의하여 공격과 리소스 남용 방지
사전 설정된 3가지 DDoS 공격 방지 모드를 사용할 수 있으며, 다양한 유형의 공격을 대응하기 위해 쉽게 전환 가능
L3/4 및 L7 DDoS 공격 경고를 포함한 웹 사이트 내 이상 감지 시 신속하게 알릴 수 있는 종합 모니터링 및 경고 서비스
HTTP/HTTPS 및 TCP/UDP 프로토콜 지원
비즈니스 요구사항에 가장 효과적인 방법으로 지급할 수 있도록 위험 조건을 기반으로 설계된 유연한 가격 모델을 제공합니다. 예산에 따라 무제한 방어와 탄력적인 방어 플랜 중 선택할 수 있습니다.
씨디네트웍스는 오리진 서버의 실제 IP 주소를 완벽하게 가려 서버 보안을 강화합니다. 이로 인해 공격자는 오리진 IP를 식별할 수 없으며 오리진 서버를 직접적으로 공격할 수 없습니다. 또한, 불필요한 요청을 차단하고 보안 수준을 강화하기 위해 화이트리스트에 추가할 글로벌 PoP의 IP를 제공합니다.
CDNetworks 콘텐츠 전송 네트워크(CDN)는 수천 개의 글로벌 대기업에 서비스를 제공하고 대량 액세스 데이터 및 공격/방어 샘플을 포함하여 매일 TB 규모의 로그 데이터를 처리합니다. 플랫폼의 빅데이터 및 머신 러닝 기능은 네트워크 공격 동향을 실시간으로 감지하고 사전에 자동으로 방어를 활성화합니다. 또한 공격을 지능적으로 분석하고 식별하여 IP 주소, HTTP 헤더, 쿠키, JavaScript 스니펫 등 합법적인 트래픽의 정상적인 동작을 모델링합니다.
씨디네트웍스는 서비스와 애플리케이션을 보호하기 위해 DDoS 보호, 웹 애플리케이션 방화벽(WAF), API 보안 및 게이트웨이, 봇 관리 및 특정 공격 편향 모듈을 포괄하는 포괄적인 다계층 보안 솔루션을 제공합니다. 여러 제품에 단일 포털을 사용하면 유지 관리 비용을 크게 절감하고 팀 운영을 단순화할 수 있습니다.
20개 이상의 글로벌 DDoS 스크러빙 센터와 15Tbps의 총 용량을 갖춘 Flood Shield는 가장 정교하고 대규모의 대량 공격으로부터 웹사이트와 네트워크 인프라를 보호하도록 설계되었습니다.
글로벌 서버
글로벌 CDN PoP
대상 국가 및 지역
스크러빙 용량
스크러빙 센터
Flood Shield DDoS 방어 기술은 씨디네트웍스의 분산 PoPs 내 배포되어 있습니다. 클라우드 기반의 "always-on" 방어 서비스로 처리량은 사실상 무제한입니다. 기업의 네트워크를 복잡하게 구축 및 변경이 필요하지 않으며, 투명한 자동화를 제공합니다.
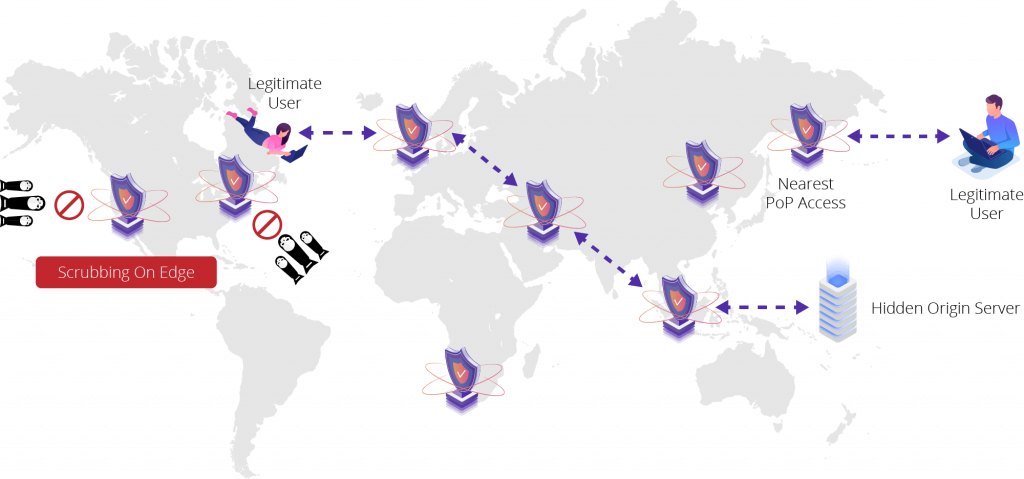
Flood Shield는 간단한 DNS 변경을 통해 일반적으로 웹 사이트, HTTP/S 트래픽 및 다양한 도메인, 서버, 프로토콜을 포함한 전체 네트워크 인프라를 보호합니다. 고객 트래픽은 씨디네트웍스의 PoP을 통해 라우팅되어, 기업의 서버와 네트워크가 아닌 씨디네트웍스 인프라로 DDoS 공격이 가해집니다. 씨디네트웍스의 PoP은 애플리케이션 계층 공격 (L7) 및 알려진 모든 유형의 네트워크 계층 공격(L3/L4)을 모두 탐지하고 차단합니다.